ITRS Log Analytics for Security
A question we are frequently asked is what are Security Information and Event Management systems (SIEM) and what role do they play in our IT infrastructure. While this may be a simple question, the answer can be complicated.
SIEM systems vary greatly depending on how they are applied. In the past they have predominantly been a monolithic system, where logs from predefined sources were analysed and checked for suspicious behaviour. This approach can still be seen among the majority of products currently on the market. The problem with this approach is that every log source from the compatibility list is covered with an array of detection rules to give the impression that the product is ready to go from the start. However, in reality this readiness is causing an increasing number of issues as majority of log sources are not in line with the compatibility list due to firmware changes, wrong specifications or differences in localizations.
Working with a complex and changing source is not an easy task for regular SIEM. ITRS Log Analytics takes this custom approach. With the ease of adding unlimited data to the platform we are able to address security use cases one by one. We have learned from our customers that the most important part for SOC’s is the ability to work on large set of data. ITRS Log Analytics is ready to handle this. Our single log analytics node is able to handle up to a thousand of events per second and clustered setup can easily multiply that number. ITRS Log Analytics can work with any text source coming from Windows events, syslog, application logs, json, csv, api calls, netflow plus integration with custom and API sources – that is our key selling point.
Close integration with IT operational data in ITRS Log Analytics allows us to run our own queries on top of the entire dataset. As a result, a complicated task such as searching through hundreds of terabytes is made simple.
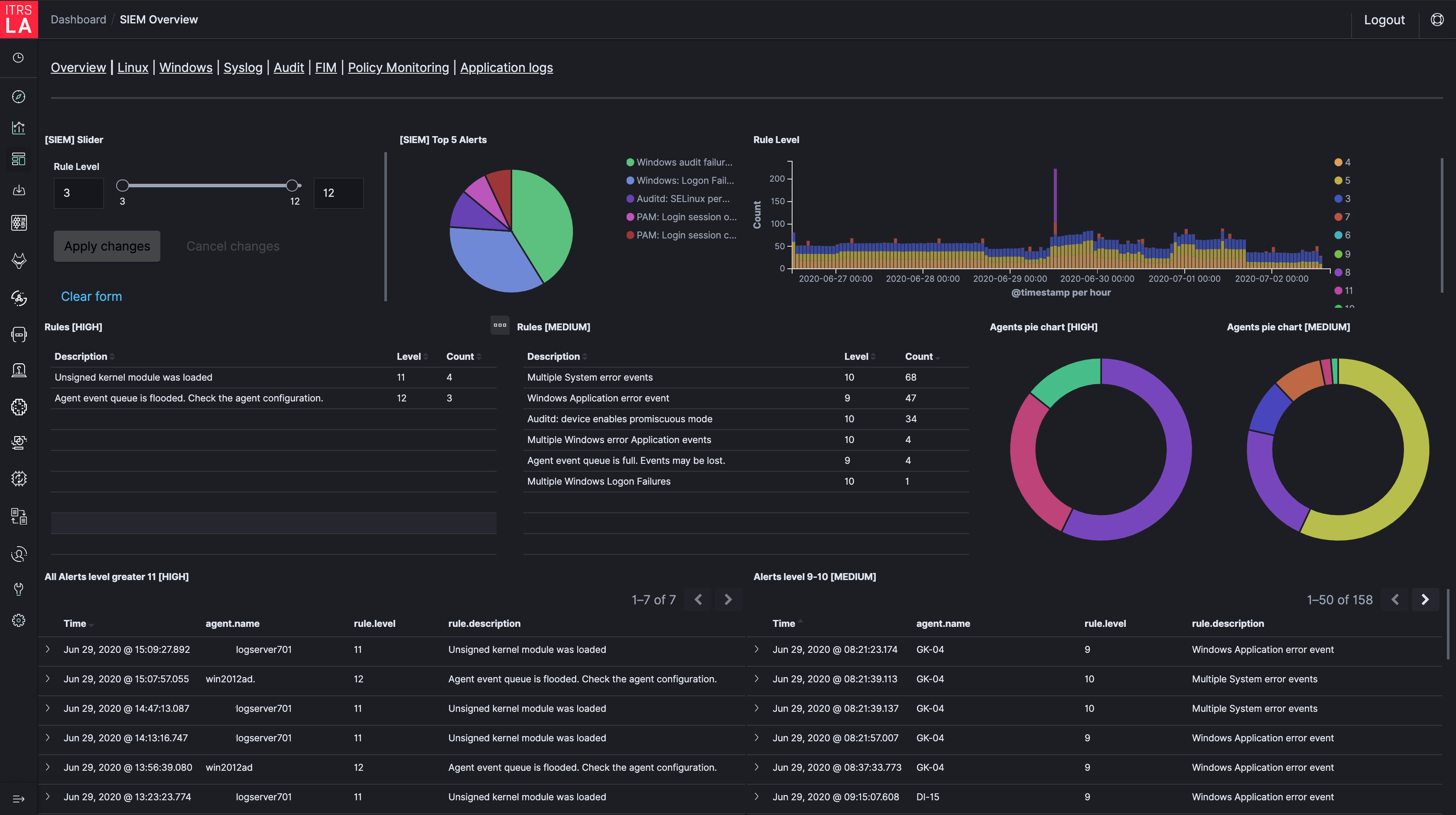
Knowledge about your own data and ability for running complex searches is a must while building proper security picture. Every search we run and every expression we look for can now be automated inside alerting engine. ITRS Log Analytics comes with rich list of detection rules that helps to track changes in the data.
There are simple ones like:
• Frequency rule – triggers when a log count is lower/higher than the threshold – detection of massive DDOS or brute force atack
• Spike rule – triggers when a log count is lower/higher than the baseline – detection of rapid change in application error count
• Any – triggers when there is a match in search syntax – detection of every error code
And more complex:
• New term – triggers whenever there is a new value in our data – detection of file changes or discover new device in subnet
• Long term – detects subset of data in corresponding time windows – detection of long sessions
Finally everything is in one place : we have all the data, alerts are configured for automatic detection and our SOC team is ready to start working on sophisticated dashboards. Live data is correlated with ‘Indicators of Compromise’ list, which is automatically updated. Bad IPs, malicious urls, malformed domains are recognised in real time, delivering a dynamic picture of recent security threats.
ITRS Log Analytics can store massive amount of data that makes it possible to act in a variety use cases, where operating as a SIEM being the most common method of deployment.