Alerting for Real Time IT Logs
Without a doubt, it’s important to ask yourself: how much do you know about your IT environment? When something goes wrong, are you the first to know about it? Are you able to detect patterns among tens or hundreds of thousands of regular events? Would you know if there was a security breach straight away?
Not all of these questions can be answered by people alone, that’s what ITRS Log Analytics is for! Log Analytics continuously monitors systems to identify performance highs and lows, provides security checks and alerts for any violation of any defined rule set by the user. Because it gathers all your performance data, security events and application logs in one place, you can easily identify an issue before it becomes a problem.
In an always-on economy it has become increasingly important to be able to identify potential threats and changes in real time. Our new and powerful alerting module is equipped with a number of different rules for different tasks. Including a number of detection rules such as: metric aggregation, frequency checks, spikes and flatlines, single value search and value change. All of which can be automated to work on real time data streams to allow you to react to any and all changes in your data.
Because it’s fully configured from GUI level and with lots of predefined rules, our new alert module is delivered within the system. This flexible approach allows users without any programming knowledge to improve existing alerting rules, or create entirely new ones. And if you are an admin who prefers console over GUI – we cater to you as well, with alerts and configurations being easily managed from the console level too.
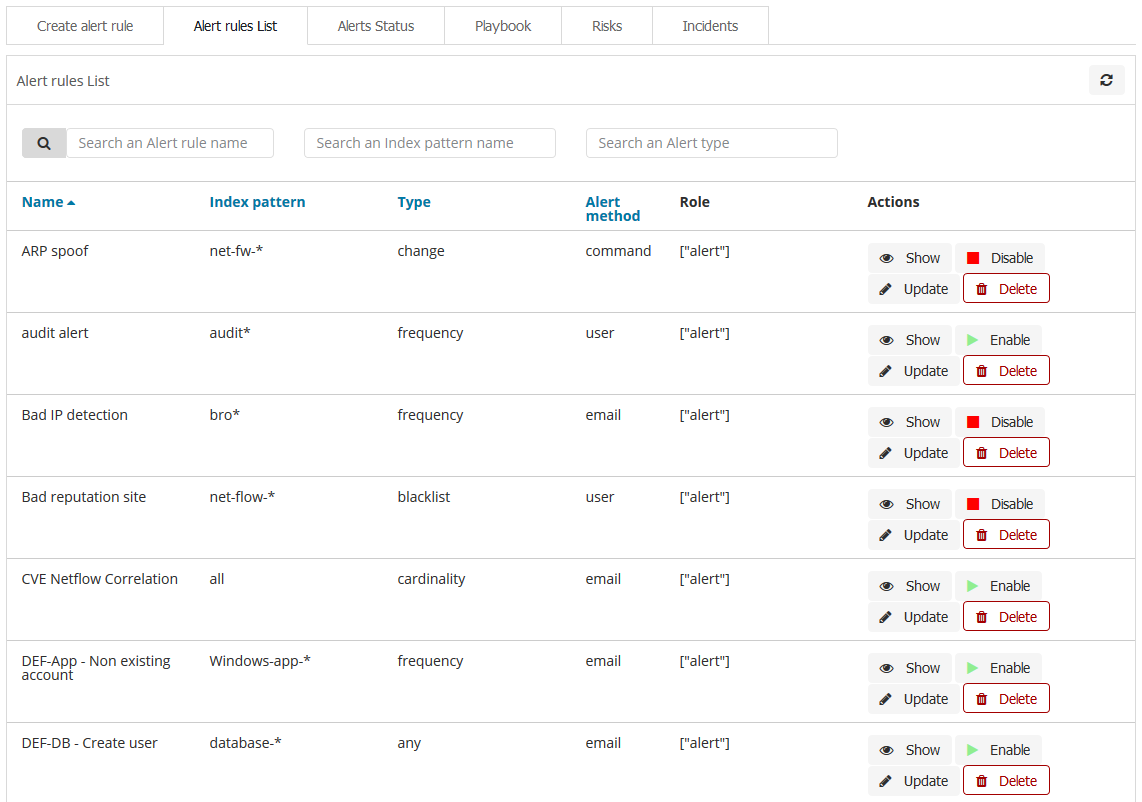
Alerts can react to many security aspects in your logs. Typical use case for alerts is detection of:
● Multiple failed logins
● Password changes
● User update
● GPO Policy change
● Admin works outside business hours
● Files Integrity Violation
● Application errors
● Firewall rule changes
● New software installation
● Bad IP recognition
● and many others
Once alerts are configured the system is no longer a log collection tool but work as SIEM.



